Losing track of valuable equipment, experiencing costly thefts, or facing non-compliance penalties can cripple a business. But worry not! Security labels offer a powerful and versatile solution to these challenges. They help you quickly identify tampered products.
That’s why investing in security label solutions is the best bet for businesses to strengthen their product security and guarantee that their goods reach consumers free from tampering or counterfeiting. This article explores the various types of security labels and how they contribute to comprehensive asset protection.
Why Use Security Labels? Key Benefits for Your Business
Security labels, or security tag stickers, are specialized stickers or tags designed to protect valuable assets and prevent tampering, theft, or unauthorized access. With tamper-evident adhesives and other features, these labels provide an added layer of security—making it easier to detect any unauthorized removal or tampering attempts.
Here are a few more benefits of security labels:
- Provide Tamper Evidence: Clearly show unauthorized access.
- Deter Theft & Counterfeiting: Make illicit activity riskier and harder.
- Enable Asset Tracking & Traceability: (Mention Barcodes, QR Codes, RFID here).
- Enhance Brand Trust & Authenticity: Assure customers of genuine products.
- Ensure Compliance: Meet industry regulations (e.g., pharma, electronics).
Made from a variety of materials like paper, vinyl, or aluminum, security labels are highly customizable. They can be printed with logos, designs, or security features like barcodes and QR codes, enhancing brand recognition and security.
These secure labels are commonly applied to a wide range of items, including electronics, packaging, and high-value products, offering both visible and covert security solutions. In industries where asset protection is vital, such as retail, warehousing, and logistics, security labels are an essential part of the overall security strategy.
The 5 Main Types of Security Labels
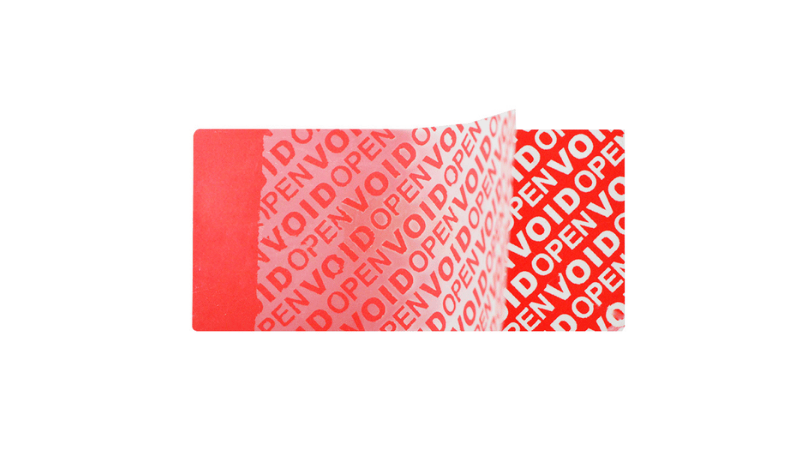
1. Tamper-Evident VOID Labels

Void labels use a specialized adhesive and label construction to create a tamper-evident seal. The adhesive is formulated to leave a distinct “VOID” or “OPENED” imprint on the surface to which it’s applied when removed.
This irreversible marking provides irrefutable evidence of tampering, even if the label itself is removed cleanly. The clarity and permanence of the message ensure that any unauthorized access is immediately apparent. The design and materials used in void labels are carefully selected to resist removal without leaving a visible indicator, providing a reliable and tamper-proof seal.
Features:
- Leaves a “void” or “opened” message when removed
- It cannot be reused once removed
- Easy to apply to boxes and containers
Applications:
Void labels are widely used in packaging and shipping across industries such as electronics, cosmetics, and retail. Various sizes and materials are available to accommodate different packaging types and applications.
Tamper-Evident Stickers

The main purpose of these security labels is to show if someone has opened a product without permission. When these stickers are taken off, they leave glue or make marks so that they can’t be put back on cleanly. This shows that they have been peeled open already.
Features:
- An adhesive that leaves a trace upon removal
- Cannot be reused once removed
- Provides clear visual evidence of tampering
Applications:
Tamper-evident stickers are widely used in industries like food, beverage, and pharmaceuticals to ensure product safety and consumer protection. These stickers play a crucial role in preventing the unauthorized opening of packages, helping businesses comply with regulatory standards, and ensuring the integrity of products on store shelves.
3. Holographic Security Labels

Holographic security labels incorporate complex, three-dimensional holographic images that are extremely difficult, if not impossible, to replicate without specialized and expensive equipment. The unique and complex nature of these holographic designs acts as a powerful deterrent against counterfeiting, making it far less attractive for criminals to attempt to reproduce the labels.
Features:
- Holographic or 3D images for enhanced security
- Difficult to replicate or forge
- It can be customized with logos or brand-specific designs
Applications:
Holographic security labels are frequently used in high-end retail packaging, luxury goods, and electronics to prevent counterfeiting. These labels also serve as a powerful marketing tool, enhancing the perceived value of premium products.
4. RFID / NFC Labels (Smart Labels)

RFID (Radio Frequency Identification) tags and labels are created for the purpose of following products through the supply chain or stocktaking. These labels use radio waves to transmit data to a reader, even if the tag is concealed within packaging or stacked among other items. This enables continuous monitoring of product location and movement, providing invaluable insights into inventory levels, transit times, and potential bottlenecks.
Features:
- Radiofrequency transmission for real-time tracking
- Can store data such as product details and location
- Non-contact scanning for efficient inventory management
Applications:
RFID tags and labels are commonly used in industries where tracking products and managing inventory efficiently is critical. They are perfect for logistics, retail, and manufacturing sectors, enabling businesses to monitor goods throughout their supply chain and reduce the risk of theft or loss.
5. Security Tape (Label Format)

Security tape is a type of sticky material used for closing boxes, parcels, or holders. It is made in such a way that it either splits noticeably or causes some noticeable damage whenever meddling happens. These characteristics are helpful since they help show if things have been messed with while being transported or kept in storage facilities, hence making security tape labels a fundamental product.
Features:
- Breaks or leaves a mark upon tampering
- Easy to apply to boxes and packages
- Available in various sizes and designs
Applications:
Security tape is often used in logistics and shipping to seal packages and ensure that they remain intact during transit. To double-check that their packages have not been tampered with, businesses use security tape as an added layer of protection.
How Security Label Technologies Work

Security labels are designed to be compatible with various Electronic Article Surveillance (EAS) systems and frequencies, such as RF 8.2MHz and AM 58KHz. This compatibility enables the integration of security labels into existing security infrastructure in retail environments, warehouses, and distribution centers. The technologies used in security tag stickers enhance overall asset protection efforts, ensuring that products are safeguarded from theft and tampering across different stages of the supply chain.
Here are the technologies used in security labels explained in detail:
Tamper-Evident Adhesives & Constructions
Tamper-evident technology is the main component of security labels. It’s designed to leave visible traces whenever someone tries to remove or interfere with the label, alerting anyone who handles the product that it has been compromised. Whether through a special adhesive that leaves a residue or labels that fracture into pieces, this technology makes it obvious when unauthorized access has occurred.
RFID/NFC
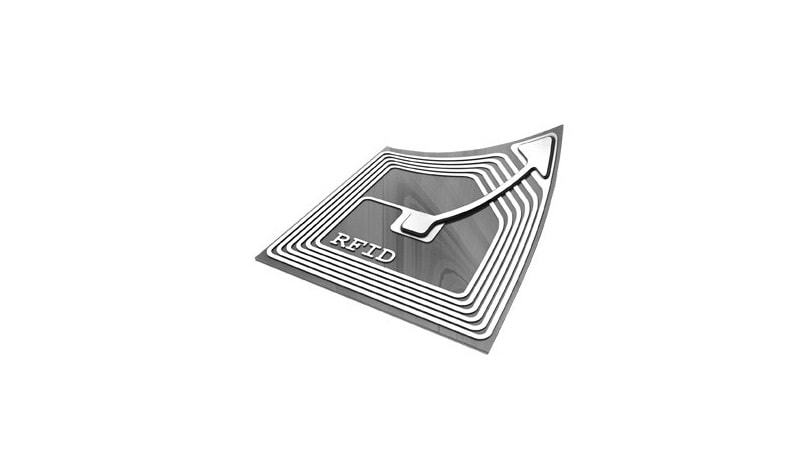
RFID (Radio Frequency Identification) and NFC (Near Field Communication) are technologies integrated into security labels to store and transmit data. These labels are equipped with a small chip that can be scanned wirelessly to track a product throughout the supply chain.
RFID labels are commonly used for inventory management, asset tracking, and to prevent theft by providing real-time data on the location and status of the product. NFC labels, on the other hand, allow for closer proximity scanning, which is often used in customer interactions and product authentication.
Holography

Holographic technology involves the creation of 3D holograms or intricate patterns that are extremely difficult for counterfeiters to replicate. Holography is a dynamic visual element that changes under different lighting conditions. The shifting visual effect serves as a powerful deterrent to fraud, making it easily noticeable if the product has been tampered with. Holographic technology reinforces the authenticity of the product, providing consumers with confidence in its genuineness and increasing its perceived value.
How to Choose the Right Security Label Solution?

When selecting a security label solution, businesses must consider specific industry or product requirements. Different industries may have varying needs in terms of security features and compliance, so it’s essential to evaluate the best solution based on those criteria.
For example, retailers may require labels with RFID technology to track inventory in real-time, while manufacturers may prioritize tamper-evident features for quality control. Evaluating label material, size, and shape options is also crucial.
Security labels come in various forms to accommodate different types of packaging, from small, discreet labels for high-end retail items to larger, more durable labels for industrial products. The right material should be chosen based on its ability to adhere securely to the product while maintaining durability.
Another key consideration is the assessment of security features and technologies needed. Depending on the level of protection required, businesses may choose labels with advanced features such as RFID, NFC, or holographic effects. These technologies help provide enhanced security, traceability, and ease of verification.

Finally, comparing prices and costs associated with different label solutions is essential. Security labels come in various price ranges depending on the features, materials, and customization options. Businesses should weigh the price against the level of security and functionality offered to find the ideal solution for their needs.
Implementation and Best Practices for Security Labels
Proper application and placement of security labels are vital to ensure their effectiveness. Labels should be strategically placed on packaging or products in a way that makes tampering or removal obvious. Consistent and accurate placement during manufacturing or packaging is essential to maintain product integrity.
Training employees on label usage and handling is another important aspect of implementing security labels. Workers should be educated on how to apply, inspect, and manage security labels, ensuring that all processes are followed correctly. This will help reduce errors and improve overall efficiency.
Regular inventory audits and label verification are also key practices to ensure ongoing security. By conducting routine checks of product labels, businesses can quickly detect any signs of tampering or unauthorized access. This proactive approach helps maintain product protection throughout the supply chain.
Lastly, businesses must secure the storage and disposal of unused or damaged labels. It is important to store security labels in a safe, controlled environment to prevent theft or misuse. Any damaged or outdated labels should be securely disposed of to maintain the integrity of the security system. Regular audits of label stock can also ensure that only valid labels are in circulation, reducing the risk of counterfeit or compromised products reaching consumers.
Case Study: How Security Labels Reduced Counterfeiting for an Electronics Retailer
Security labels have proven to be a game-changer for many industries, providing robust solutions to asset protection, compliance, and theft prevention. A major electronics retailer, facing significant losses due to counterfeit products and fraudulent returns, implemented holographic security labels on high-end devices like smartphones and laptops.

These labels, featuring intricate, unique designs difficult to replicate, served as a powerful deterrent against counterfeiting and a verifiable proof of authenticity for consumers. The results were striking:
- Significant Reduction in Counterfeit Products: The retailer experienced a dramatic decrease in the number of counterfeit products entering their supply chain and reaching their shelves. This was achieved through a combination of deterrence (making counterfeiting more difficult) and detection (easy verification of authenticity).
- Improved Consumer Trust and Brand Loyalty: Customers appreciated the added assurance provided by the holographic labels. The ease of verifying product authenticity fostered greater trust in the retailer and its products, leading to increased customer satisfaction and brand loyalty.
- Reduced Fraudulent Returns and Product Tampering: The visible tamper-evident nature of the labels significantly reduced fraudulent returns and instances of product tampering. Customers were less likely to attempt to return counterfeit or tampered-with products, knowing that any attempt to remove or alter the label would be immediately apparent.
- Enhanced Supply Chain Security: The implementation of holographic labels also improved the overall security of the retailer’s supply chain. By identifying and preventing counterfeit products from entering the supply chain, the retailer minimized losses and protected their brand reputation.
The financial impact of this initiative was equally impressive. The reduction in counterfeit goods, fraudulent returns, and associated investigation costs resulted in a significant return on investment (ROI). Furthermore, the improved brand reputation and increased customer loyalty translated into sustained long-term growth and profitability.
This case study underscores the significant value proposition of security labels: a cost-effective solution that delivers substantial returns by protecting assets, enhancing brand reputation, and ultimately driving business success.
Compliance and Regulatory Requirements
Ensuring compliance with industry regulations and standards is essential for maintaining product integrity and safety. Security labels must adhere to various recognized standards, such as ISO (International Organization for Standardization) and ANSI (American National Standards Institute).

These standards ensure that security labels meet minimum requirements for quality, durability, and effectiveness. By following these guidelines, companies can confidently provide products that comply with safety and regulatory measures, reducing the risk of fines, recalls, and other legal issues.
Certain industries have specific labeling requirements to ensure the safety and authenticity of their products. For instance, the pharmaceutical, food and beverage, and electronics sectors often have strict guidelines that security labels must meet.
These regulations can cover everything from labeling materials to printing methods, and it’s important for companies to ensure that their security labels meet these standards. Failure to do so can result in non-compliance penalties or legal action, making it essential for businesses to stay updated on these requirements.
Security Label Trends and Innovations
Security labels are evolving with advancements in technology, particularly through the integration of the Internet of Things (IoT). Smart labels equipped with RFID or NFC technology enable real-time tracking and monitoring, providing businesses with valuable insights into their assets.
This integration enhances security by offering instant alerts about tampering or unauthorized access, improving inventory management, and reducing loss. In addition to technological innovations, sustainability is becoming a key trend in security labels.
More businesses are opting for eco-friendly materials such as recyclable, biodegradable, and plant-based options, aiming to reduce environmental impact. Alongside this, the ability to customize security labels with logos, brand messages, and advanced security features has grown, allowing companies to strengthen both product protection and brand identity while enhancing consumer trust.
FAQs
Q1: Do security-protected stickers work?
Yes, security stickers are effective at deterring theft and tampering. They leave visible signs if removed or altered.
Q2: How do security stickers get deactivated?
Security stickers are deactivated using special scanners or devices at checkout to prevent triggering alarms.
Q3: How do you take off security stickers?
Security stickers can be removed using heat (e.g., a hairdryer) or adhesive remover, though they may leave residue or marks.
Conclusion
Security labels are an absolute necessity to protect your valuable products. And while there’s an initial investment in tamper-evident technology, the long-term return on investment (ROI) is substantial. Consider the costs associated with product theft, counterfeiting, recalls, and damaged brand reputation. Security labels significantly mitigate these risks, leading to substantial cost savings.
Lead the Way With Shosky Security Labels!
At Shosky Security, we specialize in providing top-tier tamper-evident solutions that cater to various industries, from banking and electronics to packaging and logistics. For personalized solutions or to discuss your security requirements, contact us and let us help you safeguard your business with the best tamper-evident technologies available!

